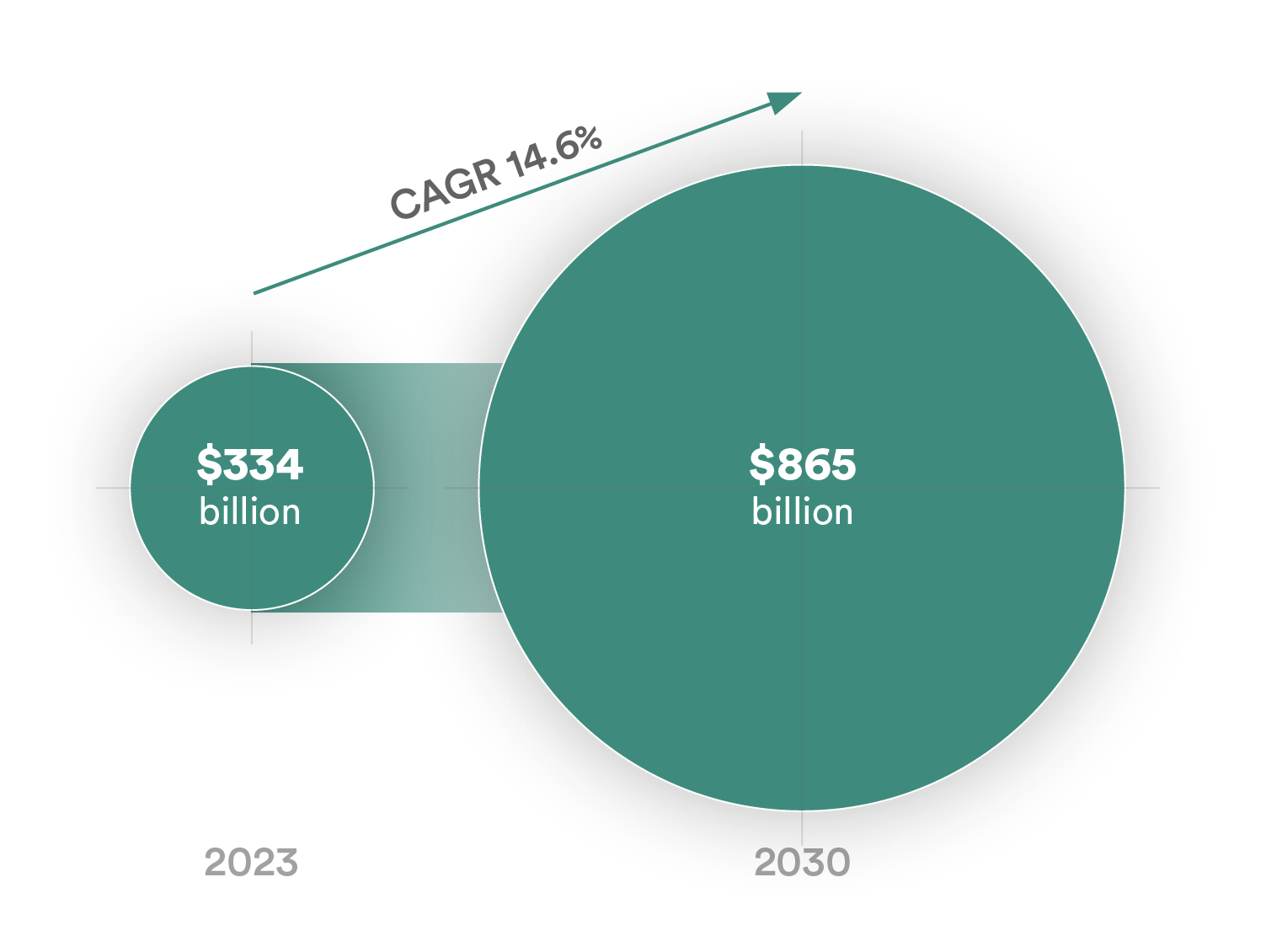
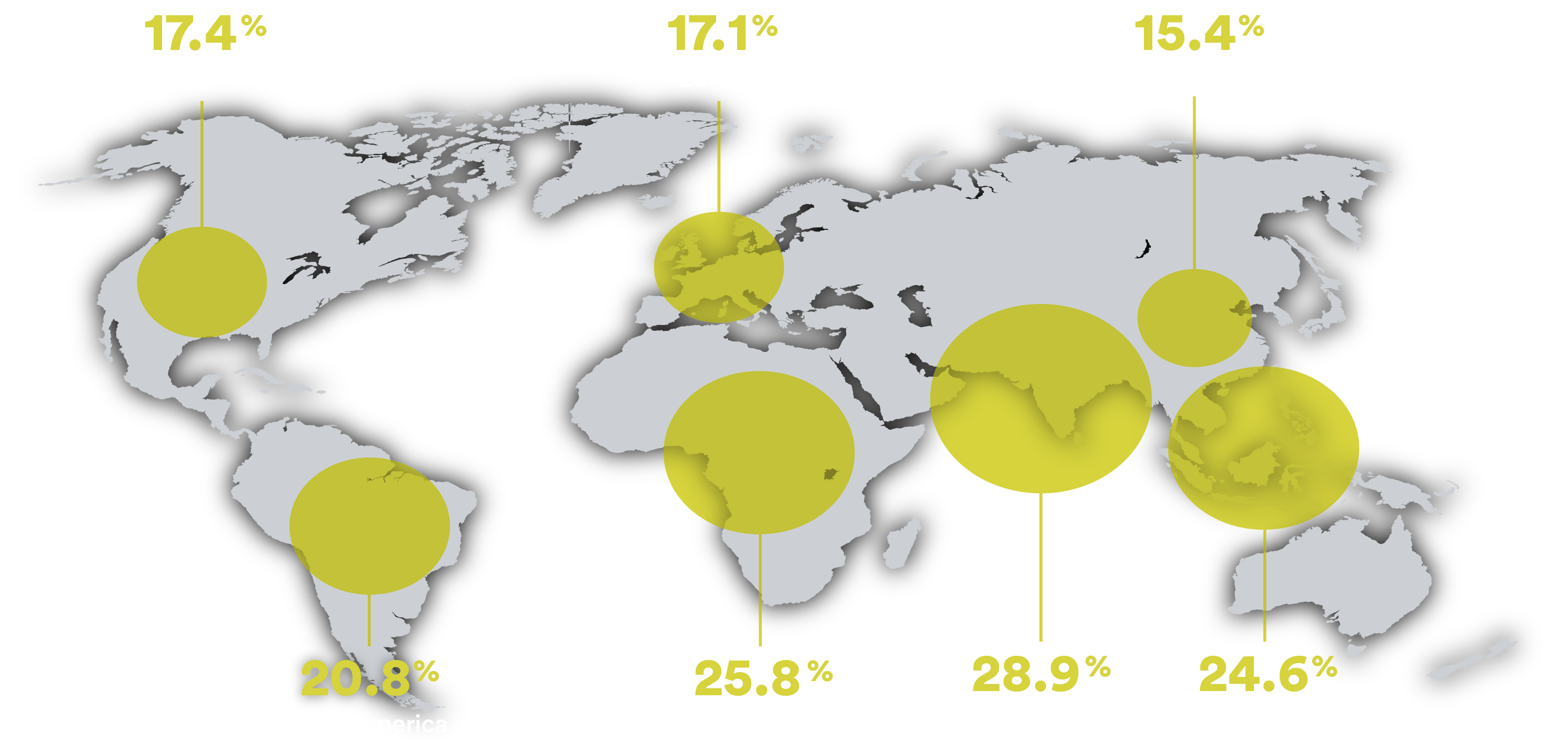
When it comes to securing your IoT devices, the best SSH IoT anywhere is the ultimate game-changer. Imagine having a secure, reliable, and scalable solution that keeps your data safe, no matter where you are. This isn’t just about protecting your devices; it’s about giving you peace of mind in a world where cyber threats are lurking around every corner. So, buckle up, because we’re about to dive deep into the world of SSH and IoT, and trust me, you’re gonna want to stick around.
In today’s hyper-connected world, the Internet of Things (IoT) has become an integral part of our daily lives. From smart home devices to industrial sensors, IoT is revolutionizing the way we interact with technology. But with great power comes great responsibility, and securing these devices is more critical than ever. That’s where SSH comes in, offering a robust solution for managing and protecting your IoT ecosystem.
Now, you might be wondering, “What exactly is SSH, and why should I care?” Well, my friend, SSH stands for Secure Shell, and it’s like the superhero of network protocols. It provides encrypted communication between devices, ensuring that your data remains private and secure. Whether you’re managing a fleet of IoT devices or simply want to protect your smart home, the best SSH IoT anywhere is your golden ticket to cybersecurity success.
- Lacy Kim Naked A Sensational Journey Into Fame Fashion And Beyond
- Why Dubai Porta Potty Is A Gamechanger In Urban Sanitation
Understanding SSH: The Backbone of Secure IoT
Let’s take a step back and break down what SSH actually is. SSH, or Secure Shell, is a cryptographic network protocol that allows secure communication between devices over an unsecured network. Think of it as a secret tunnel that keeps your data safe from prying eyes. It’s not just about encrypting data; SSH also offers authentication and integrity checks, making it the go-to solution for securing IoT devices.
Here’s why SSH is so important for IoT:
- Encryption: SSH encrypts all data transmitted between devices, ensuring that even if someone intercepts your data, they won’t be able to make sense of it.
- Authentication: SSH uses public-key cryptography to verify the identity of devices, preventing unauthorized access.
- Integrity: SSH ensures that data hasn’t been tampered with during transmission, giving you confidence in the authenticity of your data.
In the world of IoT, where devices are often deployed in remote locations, SSH provides the reliability and security needed to manage and monitor them effectively. Whether you’re dealing with a few devices or thousands, SSH has got your back.
- Mothers Warmth Chapter 3 A Heartfelt Journey Through Love And Nurturing
- Tana Rain Nude Unveiling The Truth Behind The Viral Sensation
Why the Best SSH IoT Anywhere Matters
When it comes to IoT, security isn’t just a nice-to-have; it’s a must-have. The best SSH IoT anywhere offers a level of security that goes beyond the basics. It’s about creating a robust, scalable, and future-proof solution that can adapt to the ever-evolving landscape of cybersecurity threats.
Here are a few reasons why the best SSH IoT anywhere is crucial for your IoT setup:
- Scalability: As your IoT network grows, the best SSH solution will grow with you, ensuring that you can manage hundreds or even thousands of devices without breaking a sweat.
- Reliability: SSH is known for its rock-solid reliability, making it the perfect choice for mission-critical applications where downtime isn’t an option.
- Compatibility: The best SSH IoT anywhere is designed to work seamlessly with a wide range of devices and platforms, giving you the flexibility to integrate it into your existing infrastructure.
By choosing the best SSH IoT anywhere, you’re not just investing in a security solution; you’re investing in the future of your IoT ecosystem.
Key Features of the Best SSH IoT Anywhere
So, what makes the best SSH IoT anywhere stand out from the rest? Let’s take a look at some of its key features:
1. Advanced Encryption Protocols
Encryption is the backbone of any secure communication system, and the best SSH IoT anywhere takes it to the next level. With advanced encryption protocols like AES-256 and RSA-4096, your data is protected against even the most sophisticated cyber threats.
2. Public-Key Authentication
Public-key authentication is a game-changer when it comes to securing IoT devices. By using digital certificates and keys, the best SSH IoT anywhere ensures that only authorized devices can access your network, reducing the risk of unauthorized access.
3. Seamless Integration
No matter what devices or platforms you’re using, the best SSH IoT anywhere is designed to integrate seamlessly into your existing infrastructure. Whether you’re working with Linux, Windows, or macOS, you can rest assured that everything will work together like a well-oiled machine.
How to Choose the Best SSH IoT Anywhere
With so many options available, choosing the best SSH IoT anywhere can be overwhelming. Here are a few tips to help you make the right decision:
- Security Features: Look for a solution that offers advanced encryption protocols, public-key authentication, and other security features that meet your needs.
- Scalability: Make sure the solution can scale with your growing IoT network, so you don’t have to worry about outgrowing it in the future.
- Support and Documentation: Choose a provider that offers excellent customer support and comprehensive documentation, so you can get the help you need when you need it.
By doing your research and choosing the best SSH IoT anywhere, you’ll be setting yourself up for success in the world of IoT security.
Top SSH IoT Solutions on the Market
Now that you know what to look for, let’s take a look at some of the top SSH IoT solutions available today:
1. OpenSSH
OpenSSH is one of the most popular SSH solutions out there, and for good reason. It’s open-source, highly customizable, and offers a wide range of security features. Whether you’re a seasoned IT professional or a beginner, OpenSSH has something to offer everyone.
2. Bitvise SSH Server
Bitvise SSH Server is another excellent option, offering a user-friendly interface and a wide range of features. It’s particularly popular among Windows users, thanks to its seamless integration with the Windows ecosystem.
3. PuTTY
PuTTY is a lightweight SSH client that’s perfect for those who need a simple, no-frills solution. It’s free, open-source, and works on a variety of platforms, making it a great choice for budget-conscious users.
Best Practices for Securing Your IoT Network with SSH
Having the best SSH IoT anywhere is just the first step in securing your IoT network. To truly maximize its potential, you need to follow some best practices:
- Use Strong Passwords: Even with SSH, weak passwords can still be a vulnerability. Make sure to use strong, complex passwords for all your devices.
- Enable Two-Factor Authentication: Adding an extra layer of security with two-factor authentication can go a long way in protecting your network.
- Regularly Update Your Software: Keeping your SSH software up to date ensures that you have the latest security patches and features.
By following these best practices, you’ll be well on your way to creating a secure and reliable IoT network.
Real-World Applications of SSH in IoT
SSH isn’t just a theoretical concept; it’s being used in real-world applications every day. Here are a few examples of how SSH is being used to secure IoT devices:
1. Smart Homes
From smart thermostats to security cameras, SSH is keeping our homes safe and secure. By encrypting data transmitted between devices, SSH ensures that our personal information remains private.
2. Industrial IoT
In the world of industrial IoT, SSH is being used to secure critical infrastructure like power plants and manufacturing facilities. With the stakes so high, SSH provides the reliability and security needed to keep these systems running smoothly.
3. Healthcare IoT
SSH is also being used in healthcare to secure medical devices and patient data. With HIPAA compliance a top priority, SSH offers the encryption and authentication needed to meet these strict regulations.
Future Trends in SSH and IoT Security
As technology continues to evolve, so too does the world of SSH and IoT security. Here are a few trends to watch out for:
- Quantum Computing: With the rise of quantum computing, traditional encryption methods may no longer be enough. Researchers are already working on quantum-resistant encryption algorithms to stay ahead of the curve.
- AI and Machine Learning: AI and machine learning are being used to detect and respond to cyber threats in real-time, making it easier to secure IoT networks.
- 5G Networks: As 5G networks become more widespread, they offer new opportunities for IoT devices but also new security challenges. SSH will play a key role in securing these networks.
By staying ahead of these trends, you can ensure that your IoT network remains secure and future-proof.
Conclusion: Take Action Today
In conclusion, the best SSH IoT anywhere is the cornerstone of a secure and reliable IoT network. By choosing the right solution, following best practices, and staying up to date with the latest trends, you can protect your devices and data from the ever-growing threat of cyberattacks.
So, what are you waiting for? Take action today and secure your IoT network with the best SSH IoT anywhere. Leave a comment below and let us know what you think. And don’t forget to share this article with your friends and colleagues who are also interested in IoT security.
Table of Contents
- Understanding SSH: The Backbone of Secure IoT
- Why the Best SSH IoT Anywhere Matters
- Key Features of the Best SSH IoT Anywhere
- How to Choose the Best SSH IoT Anywhere
- Top SSH IoT Solutions on the Market
- Best Practices for Securing Your IoT Network with SSH
- Real-World Applications of SSH in IoT
- Future Trends in SSH and IoT Security
- Conclusion: Take Action Today
- Billie Eilish Rule 34 The Buzz The Facts And Everything You Need To Know
- How To Make Your Insta Viral Mms Video In 2024 The Ultimate Guide